Computing Crime Fighters
November 1, 2017
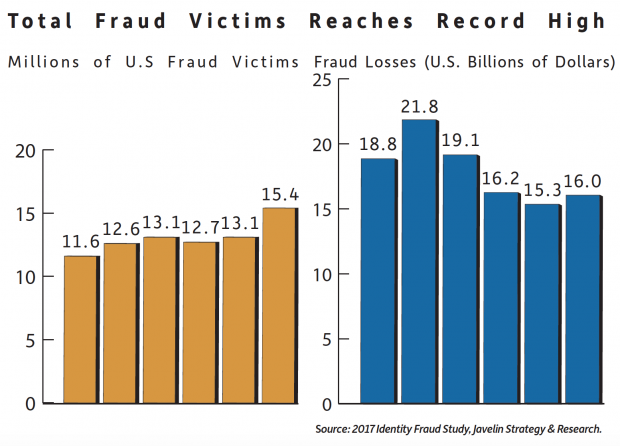
In 2016, fraudsters stole the identities off an unprecedented number of U.S. consumers—15.4 million. Then came the encore of Equifax and the Sept. 8 announcement that the consumer credit reporting agency had succumbed to an early-summer cybersecurity attack that potentially impacted 143 million U.S. consumers.
“It’s a very serious problem, and the most serious part is that we don’t know when identify theft is going to occur,” Michael Mandato, the executive vice president of System Care Inc., an IT services provider based in Cleveland, OH, says. “People have been notified that their credit cards have been stolen, that their identities have been stolen, that there’s been a breach to some of their banks. Look at Equifax. What they don’t know is when their information is going to be used. It’s not like it gets used right away. It could be sold on the black market and used six months from now. You don’t know.”
“High-performance computing is an enabling technology that allows financial institutions to use a lot more data, to use data more accurately, and to make those decisions more quickly—in other words, real time—because what they’re balancing is a good customer experience vs. managing progress.”
— David Stewart, SAS
Can the fraudsters be stopped, either in the act or, better yet, beforehand? Can high-performance computing systems play superhero vs. the dark web, where perpetrators remain anonymous or untraceable with the help of special software?
HPC’s potential to benefit the financial industry is significant, Mandato says, but “there’s all kinds of compliance that we have to meet.” Such an aim is always more difficult to accomplish than it sounds, he adds, noting that 61% of the breaches in identity fraud cases are caused by stolen credentials. “If we’re passing compliance, then why do we still have breaches?” he says.
The financial industry is particularly vulnerable to cyberattacks because of its involvement in technologically demanding operations, such as high-frequency trading, real-time analytics, and complex financial modeling, as well as sophisticated fraud detection and security processing. Tasks such as these, according to “High Finance, Harnessing the Power of HPC,” a CDW Corp. white paper, demand cutting-edge computing that can process large data flows, detect patterns, assess risk, project value and drive profit.
HPC fits the bill, CDW writes, because its powerful multicore processors and parallel storage combine with fast, low-latency networks, reducing time to action and enabling more effective analysis. For example, HPC enables instant execution of high-frequency, algorithmic trading to leverage fleeting market opportunities that result in gains. The technology delivers advanced analytics, allowing firms to detect, assess and manage risk factors in complex markets.
“High-performance computing, in general, assists us in mitigating fraud risk because it allows us to make decisions much faster,” David Stewart, the director of financial crimes and compliance at SAS, says. “If we want to decide if an online or mobile banking session is potentially fraudulent or suspicious, we can make those decisions faster. High-performance computing allows us, particularly in model development and model deployment, to run many, many more iterations of models so that we arrive at more accurate predictive analytics, so that not only do we make decisions faster but we also make decisions on the right people or, in the case of fraudsters, the wrong people. We’re more accurately predicting those sessions or those payments that may be fraudulent, in essence reducing false positive rates.”
One Step Forward, Two Steps Back
Identity fraud is defined as the unauthorized use of another person’s personal information to achieve illicit financial gain. It can range from simply using a stolen payment card account, to making a fraudulent purchase, to taking control of existing accounts or opening new accounts.
Javelin Strategy & Research, a research-based advisory firm in Pleasanton, CA, breaks down the nightmare that was the previous year in its 2017 Identity Fraud Study. Four trends stood out, it reports:
- Fraud jumped to a record-high incidence—In 2016, 6.15% of consumers became victims of identity fraud, an increase of almost 2 million victims from the previous year. The incidence rate jumped by 16% from 2015, the highest incidence since Javelin began tracking identity fraud. This increase was driven by growth in existing card fraud, which saw a significant spike in card-not-present transactions.
- Card-not-present (CNP) fraud rose significantly—Driven by closing opportunities for point-of-sale fraud and the growth of e- and m-commerce, fraudsters are increasingly moving online, dramatically increasing the prevalence of CNP fraud by 40%. Meanwhile, incidence of fraud at the point-of-sale (POS) remained essentially unchanged from 2014 and 2015 levels.
- Account takeover (ATO) bounced back—After reaching a low point in 2014, account takeover incidence and losses rose notably in 2016. Total ATO losses reached $2.3 billion, a 61% increase from 2015, while incidence rose 31%. Account takeover continues to be one of the most challenging fraud types for consumers, with victims paying an average of $263 out-of-pocket costs and spending a total of 20.7 million hours to resolve it in 2016—6 million more than in 2015.
- New-account fraud continued unabated—As EMV cards (Europay, MasterCard and Visa; aka chip cards) and terminals continue to permeate the U.S. POS environment, fraudsters shift to fraudulently opening accounts online. At the same time, fraudsters have become better at evading detection, with new-account fraud (NAF) victims being notably more likely to discover fraud through review of their credit report (15%) or when they were contacted by a debt collector (13%).
That the success of EMV cards otherwise worsened the landscape illustrates the savvy of identity fraud culprits and emphasizes the need to continuously adapt in the ever-evolving chess game that is fraud detection.
“After five years of relatively small growth or even decreases in fraud, this year’s findings drive home that fraudsters never rest, and when one area is closed, they adapt and find new approaches,” says Al Pascual, the senior vice president, research director, and head of Fraud and Security at Javelin Strategy and Research. “The rise of information available via data breaches is particularly troublesome for the industry and a boon for fraudsters. To successfully fight fraudsters, the industry needs to close security gaps and continue to improve, and consumers must be proactive, too.”
Hacktivists Here, There and Everywhere
Of course, battling such cybercriminals tends to be difficult when their identities are vague and their avenues almost unlimited, according to Stu Bradley, the vice president of cybersecurity solutions at SAS, a multinational developer of analytics software based in Cary, NC.
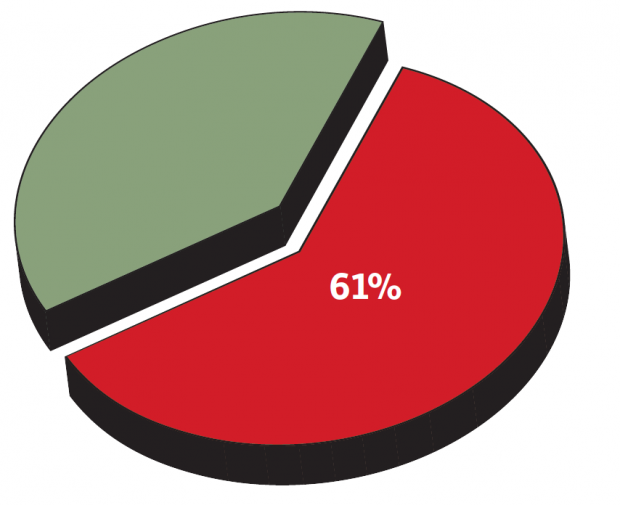 61% of the breaches in identity fraud cases are caused by stolen credentials. Source: Michael Mandato, System Care Inc.
61% of the breaches in identity fraud cases are caused by stolen credentials. Source: Michael Mandato, System Care Inc.“You have a broad spectrum that goes from nation states that might be trying to exfiltrate information from the government or the department of defense to hacktivists like Lulz Security and Anonymous, where the ‘greater good of consumers’ may be perpetrating a distributed denial of service attack on a commercial entity,” Bradley says in an SAS video. “Then you have the true cybercriminals that are looking to access information and intellectual property off of an organization’s network, such that they can monetize it through fraud on the black market. When you further think about where we’re going with mobile applications and the adoption of mobility and the concept of the Internet of Things and how all of these devices are going to be connected, it creates a great opportunity for cybercriminals to access networks. Every connected device is a potential vector to enter a network and a vulnerability that must be prevented against.”
The Bangladesh Bank cyber heist in February of 2016 exemplifies the susceptibility of networks, according to Stewart. Hackers breached the bank’s systems and used the SWIFT messaging network to order the transfer of nearly $1 billion from its account at the New York Fed. The U.S. central bank rejected most of the requests but filled some, resulting in $81 million being transferred to bank accounts in the Philippines. The money was quickly withdrawn and later disappeared in the huge casino industry in the country.
“We’ve had quite a number of breaches. If you look at the FBI statistics on business email compromise, that’s up 1,300%,” Stewart says. “Fraudsters will exploit the weakest links. The Bank of Bangladesh case is a good example.
“Fraudsters are very agile, very sophisticated. There are variants of malware that are for sale on the dark web,” he continues. “The barrier to entry is pretty small, and sophistication of this new school of coders and data scientists means we’re up against a pretty formidable threat.
“They are more often than not transnational criminal organizations,” Stewart says. “It’s not so much the individuals that present significant progress. It’s more of the very sophisticated, very technically savvy, well organized and collaborative transnational criminal threats that are perpetrating much of the fraud and much of it through malware or a cyberattack vector.”
HPC Tops the Charts in Fraud Prevention
Stewart and Bradley rank HPC No. 1 on their authored list of trends in fraud solutions, adding that HPC “redefines the possible” within the financial services sector.
“High-performance computing,” Stewart says, “is an enabling technology that allows financial institutions to use a lot more data, to use data more accurately, and to make those decisions more quickly—in other words, real time—because what they’re balancing is a good customer experience vs. managing progress.
“If you look at some of the behavioral analytic techniques, particularly anomaly detection, to deploy those we take advantage of high-performance architectures so that these models are self-learning and adaptive. Looking across a swath of transactions, a financial institution can start to spot anomalous activity. They may not catch the first fraudulent transaction, but if they see a pattern, these more advanced analytics will be able to detect the next fraudulent attempt and protect the institution and their customers from those intraday or flash attacks.”
Previously, with conventional IT platforms, it was impractical to analyze all relevant data in full context to uncover potential fraud, unless one could wait hours or days for results,” Stewart and Bradley write. However, today’s high-performance analytics “can rapidly analyze massive amounts of data, using technologies such as grid computing, in-database analytics, and in-memory analytics,” they state.
For example, simulations that once took hours now take seconds because of in-memory analytics. Fraud analysts can rapidly test multiple methods to determine which models work best. Speedier model development and testing means better models get deployed sooner, giving institutions more agile response to the flash fraud and zero-day threats that can manifest in online channels.
Hadoop, the open-source software framework for storing data and running applications on clusters of commodity hardware, gets credit from Bradley and Stewart for bringing high-performance data storage and processing to the fraud-fighting arsenal while operating on large clusters of commodity hardware. “Hadoop makes it fast and affordable to support analytics processes that can find anomalies in millions of records,” they write.
In turn, analytical insights can be delivered to visual interfaces and automated workflow systems. “Imagine arming your investigative team with visualizations that clarify where to look, along with supporting detail about threats as they are developing, rather than days or weeks later,” they conclude. “The end game is to have a continuous picture of active security risks in real time, intelligently prioritized for further triage and investigation. That should look good to any firm that wants to avoid making headlines for a high-profile breach.”
The Need for Quality Data
HPC poses a number of challenges that must be addressed to ensure optimal return, according to the CDW white paper. From the early planning stages, IT and business management must work together closely to develop a plan that meets the functional requirements of the business and results in an HPC buildout that can adapt to changing needs. Other considerations, per CDW, include the following:
• Software first: HPC can deliver advanced performance, but it needs advanced software to do it. Tailored management and security tools tuned for parallel processing are required. Existing applications may need significant upgrades or replacement to thrive in an HPC environment.
- Heat, space and power: Many large HPC deployments are limited by the physical plant. Firms should carefully assess their data center facilities (and potential future needs out to five or 10 years) and consider improvements to thermal management and power delivery.
- Skills challenge: HPC clusters can place major demands on IT staff. Hiring skilled, HPC-savvy administrators, programmers and scientists remains a steep challenge.
In Stewart’s opinion, the focus remains on data.
“How do you ensure that you have good, quality data to arrive at good results? How do you ensure that you have a view of client risk? And that really requires a discipline around entity resolution, so that you know your customer and know your customer’s customer,” he says. “I also think that now that we have all this additional information about mobile devices, information about online session behavior, potentially bureau data, and other stolen information, how do we take all of that data and operationalize it to arrive at a real-time decision in less than a hundred milliseconds? Pulling all of that off, it requires a bit of discipline.”
Prevention Accomplished
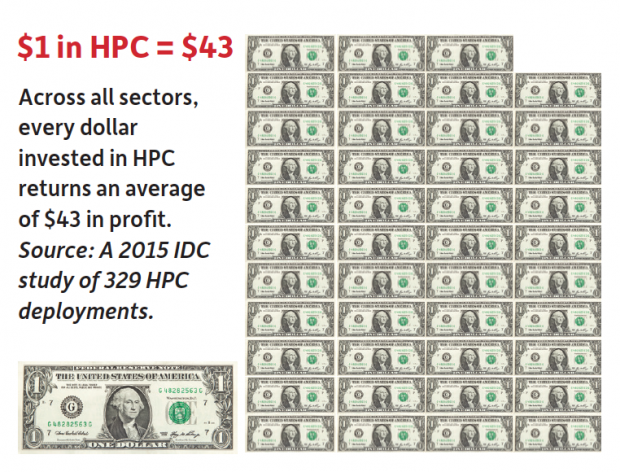
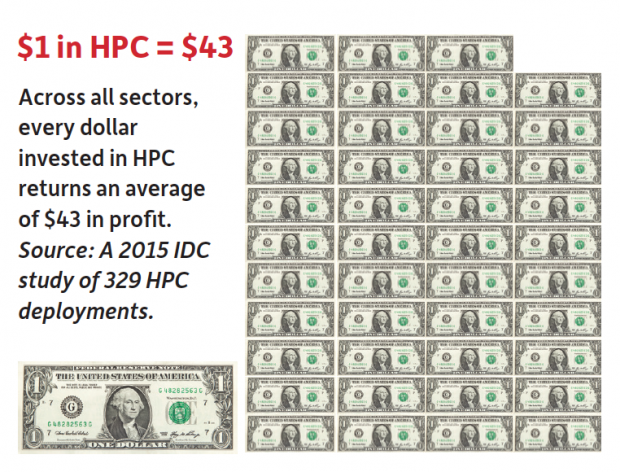
A Council on Competitiveness survey on HPC deployments found that 86% of the respondents agreed with the statement “HPC is critical to the future direction of our business.” A 2015 IDC study of 329 HPC deployments revealed that, across all sectors, every dollar invested in HPC returns an average of $515 in revenue and an average of $43 in profit.
The gains boil down to two broad categories, according to the CDW paper—speed and awareness. Speed equals profit, and clustered HPC systems offer the best solution to the equation, CDW writes. Speed also drives big yields in operational awareness. HPC enables financial firms to build more robust models, account for a greater range of variables and leverage vastly larger data sets to sharpen and broaden insight across the board.
Concludes Stewart: “Primarily these high-performance computing architectures are enabling financial institutions to deploy more sophisticated analytics that are better at identifying and preventing fraud.”
Thomas Skernivitz is a contributing editor to Digital Engineering.
More Info
Sponsored Content: Dell EMC and MasterCard Fight Cyberfraud with Machine Learning
John Walls, host of theCUBE, SiliconANGLE’s mobile livestreaming studio, sat down with Tony Parkinson, vice president of North America enterprise solutions and alliances at Dell EMC and Nick Curcuru, vice president of the big data practice at MasterCard International Inc. at Dell EMC World 2017 to discuss how the companies are staying one step ahead of cyberfraud with machine learning.
“For us, machine learning allows us to actually bring in the data so much faster,” said Curcuru, which allows MasterCard International to apply rules in milliseconds to understand which transactions are fraudulent and which are valid. “It’s not chasing; it’s ‘I am going to prevent this upfront if I can.’”
Curcuru says machine learning also reduces false positives so valid transactions by customers aren’t blocked. To do that successfully requires machine learning to “learn what you know so you can apply it to larger data sets,” says Curcuru.
MasterCard has partnered with Dell EMC to take the power of individual tools and magnify it.
“Where Dell comes into play is to provide us the ability to ... lower the cost of ownership, which gives us the ability to process faster, larger sets of data,” Curcuru says.
Watch the full video to see how MasterCard is using machine learning to add to its almost 1 million rules to detect new points of fraud, and recommendations from Dell EMC on how to begin to use machine learning.
Sponsored Content: Machine Learning at the University of Pisa
Drs. Antonio Cisternino and Maurizio Davini from the University of Pisa in Italy have been exploring machine learning using Dell EMC PowerEdge C4130 Rack Server and the PowerEdge C6320 Server Node.
“Machine learning is clearly shaping our future today,” says Cisternino, CIO for the university. “Now that the technology has matured, we have enough computational power to actually do something really useful that can be used by non-experts.”
For example, the University of Pisa is involved in research using machine learning to predict when systems will fail, to analyze images and to predict illness in patients.
“This is a very interesting period for technologies and IT, so we are trying to mix all the new technologies that are coming out to design a future-ready solution for HPC and machine learning, says Davini, the university’s CTO. “We are trying to take the best from the market and assemble a solution to support our scientific computation.”
Davini says the University of Pisa is beginning to see some nice results on image analysis in research.
“Now we have machines that learn to speak a language from zero,” Cisternino says.
Subscribe to our FREE magazine, FREE email newsletters or both!
About the Author
DE’s editors contribute news and new product announcements to Digital Engineering.
Press releases may be sent to them via [email protected].