Pushing Security from the Cloud to Every Endpoint in Today’s IoT
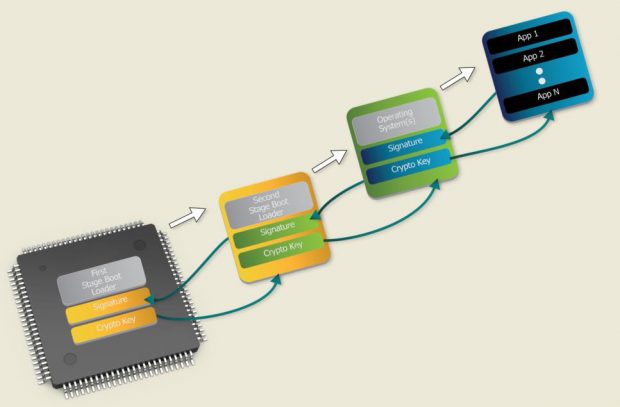
Fig. 2: Security requires establishing a chain of trust that begins in the hardware and extends to every bit of software that is loaded on the device.
November 21, 2017
By Warren Kurisu
There’s no question the connectedness behind the internet of things (IoT) has profoundly impacted our lives. Although the IoT pervades just about everything we do these days, most people are hard-pressed to define “what is the IoT”?
Different companies, different industries, even different countries seem to all have their own definition. For the sake of this discussion, let’s define IoT generally as a network of physical devices that communicate between each other and perform certain tasks they are programmed to do. These devices leverage all types of available connectivity and rely on a variety of communication protocols for safe and secure transmission. Data is transmitted from IoT endpoints (sensors, actuators, etc.) to edge devices commonly referred to as gateways or routers, up to public and private clouds where all the backend services can be connected and managed.
Early Days of IoT
The term machine-to-machine, or M2M, has been around for decades. Today’s IoT, in many respects, grew from M2M’s early beginnings. M2M architecture is characterized by isolated instances of device-to-device communication, where the devices connected using a variety of wired or wireless connections. Initially, these connections included serial, Ethernet and cellular. Typically, these devices connected point-to-point or within the confines of a local or enterprise network, but did not connect to the internet.
Today, as the internet has become more accessible and ubiquitous, devices have gained the ability to communicate using the internet via enterprise networks and service providers. This broader, internet-connected network of devices is the internet of things, which has already evolved to include the more expansive industrial internet of things, or IIoT. IoT and IIoT devices can talk vertically up and down within the IoT infrastructure (endnode-to-gateway-to-cloud) or horizontally to other devices within the same network (e.g., printer, computer, server, other mobiles devices, etc.) as depicted in Fig. 1.
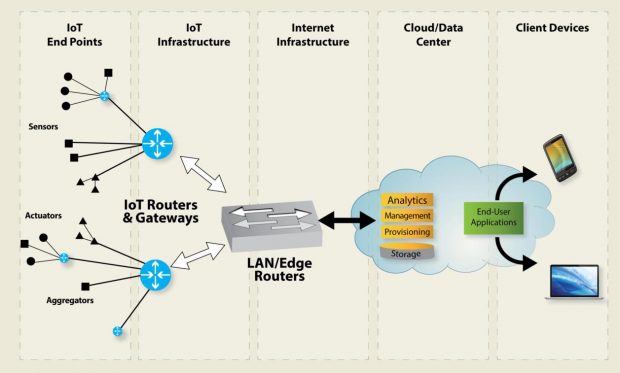 Fig. 1: IoT/IIoT connectivity includes traditional M2M connected devices, but now extends across the network, to incloud both public and private clouds along with device management capabilities.
Fig. 1: IoT/IIoT connectivity includes traditional M2M connected devices, but now extends across the network, to incloud both public and private clouds along with device management capabilities.Security: The Top Priority
As high value content now flows throughout the IoT, devices are saddled with communicating high-value information via an IoT connection. As a result, the security threat has greatly increased for all connected IoT devices.
Individual end points (e.g., sensors, actuators, medical devices, etc.) can now be accessed from the internet through enterprise connections. Now critical or private data can be stolen, or machine operations can be altered in a way that disrupts operations or worse. All of these devices have increased the surface area for a potential cyberattack.
Looking at security strictly from the IT perspective might provide some assurances of network security, but it also means you potentially need to spend enormous amounts of time configuring firewalls, managing access control lists, and ensuring security defects are addressed (e.g., Heartbleed, Shellshock and POODLE security vulnerabilities).
Thankfully, the industry is responding with a spectrum of solutions for addressing security in connected devices. These companies encompass processor IP vendors such as Arm, semiconductor vendors and Independent Software Vendors (ISVs), who are all expanding capabilities to ensure security in connected IoT devices.
Let’s take a look at security from a hardware and software perspective.
Hardware-enforced Security
Protecting data is both a hardware and a software issue now that devices are more intelligent – and more connected. Many of the most secure techniques are rooted in finding the hardware with the right security-enabled features.
Numerous stand-alone hardware security modules are available with a sophisticated and robust set of capabilities, as well as low-cost solutions having only a subset of these capabilities. For years, application processor vendors have integrated hardware security mechanisms into their devices. An example of this would Arm TrustZone technology in the Arm Cortex-A architecture.
As one moves down in performance and capability to the microcontroller level where many of today’s sensors, actuators and low-end controllers reside, it is more difficult to find advanced hardware capabilities. However, that is changing, too. Arm, for example, seems to be ahead of the curve with its Arm v8-M architecture which adds fast, low-overhead security extensions with its own built-in TrustZone technology.
So Arm is addressing hardware security that spans the IoT spectrum from the lowest-end 32-bit Arm-based devices up to the application processors that can drive the cloud infrastructure. One common use case for using a hardware security module or other hardware security mechanisms such as TrustZone, is the inclusion of secure storage of data and keys.
There have been high-profile cases where software programs were used to encrypt data on a drive. Instead of storing encrypted data deep within the hardware, the root key for decrypting everything was in a plain text file, leading to a very easy compromise or exploitation. A hardware security module protects users from these types of events. Hardware-based key storage means no one can access the security keys or crypto keys without proper permission or authorization.
Also, hardware security features must also include cryptographic capabilities and accelerators. Hardware should include a random number generator to ensure generation of cryptographic hash values.
While software-based pseudo random number generators are enough for some applications, they are not as random as true hardware-based random number generators and therefore make it easier for a hacker to compromise the system. These hardware random number generators are now available on devices from high-end microprocessors to low-end 16-bit microcontrollers. If the security provided by a software solution is enough, there are many software solutions easily accessible to developer.
Software-enabled Security
A security framework that enables quick and easy build-out of the system with robust security features is essential. This software security framework must be built on top of a system that begins execution from a high-assurance boot sequence, to ensure a chain of trust that is established by authenticating and validating the boot loader, and then extended to every other operating system, application, and software update loaded on the system (Fig. 2).
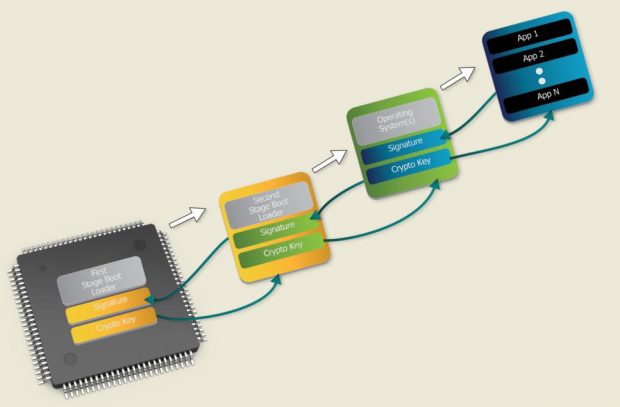 Fig. 2: Security requires establishing a chain of trust that begins in the
Fig. 2: Security requires establishing a chain of trust that begins in thehardware and extends to every bit of software that is loaded on the device.
Fig. 3 is an architectural view of an embedded security framework created by Mentor tailored for Industrial IoT (IIoT) devices. It was built to run on devices that require the determinism of a real-time operating system (RTOS) or the capabilities of Linux – and to solve many issues around embedded security.
With it, software developers can utilize secure boot, secure remote firmware updates, and managing keys and certificates. The framework’s scalability provides basic foundational security on tiny devices within IIoT end points, such as sensors or actuators that are built on small, low-power eight-bit microcontrollers – up to more complex devices that require more capabilities such as device management and monitoring.
 Fig. 3: Mentor’s complete security framework leverages hardware security features, platform capabilities, along with security features from Icon Labs.
Fig. 3: Mentor’s complete security framework leverages hardware security features, platform capabilities, along with security features from Icon Labs.Conclusion
The IoT as well as the IIoT present a complex set of challenges for the modern software developer. Security is needed everywhere. Devices are everywhere, and the devices themselves are evolving to perform a new set of capabilities and tasks. Machine intelligence in industrial environments is now being pushed from the cloud toward the edge. As a result, increasing amounts of data are now being stored in end points and edge devices.
The bottom line is IoT security is far too complex to go out and build a few security blocks here and there. You simply cannot risk a security breach with connectivity so pervasive in so many different devices. And increasingly, the devices up and down the IoT infrastructure are handling more sensitive and critical data.
Warren Kurisu is the director of product management in Mentor’s Embedded Systems Division, overseeing the embedded runtime platform business for the Nucleus RTOS, Mentor Embedded Linux, virtualization and multicore technologies, safety certified runtimes, graphics and development tools. Warren has spent nearly 30 years in the embedded industry, both as an embedded developer and as a business executive, working broadly in industries including aerospace, networking, industrial, medical, automotive, and consumer.
For more info, visit Mentor.
Subscribe to our FREE magazine, FREE email newsletters or both!