Latest News
April 21, 2011
If ease of use and low learning curve are the desired attributes of a good human-machine interface, then the ideal interface has to be an invisible one. No buttons to push, no menus to navigate, no commands to type. The machine, or the computer, deduces your requests from your normal gestures and natural language, then deliver the data confidentially to your eyes, for your eyes only.
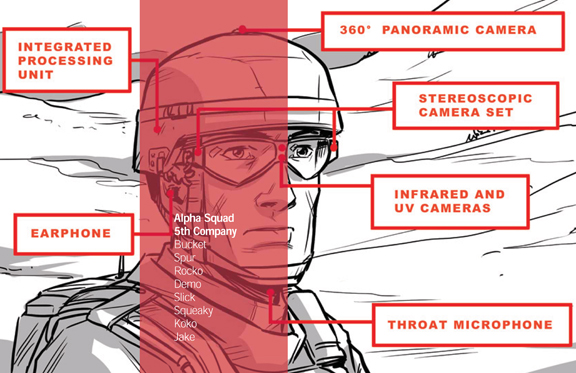
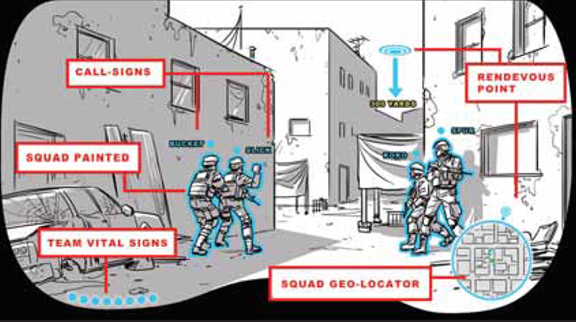
Sounds too far-fetched? Too Star Trek, too James Bond? Not at all. Such interfaces have been in the field, in operations for quite some time now. The headgear of a modern soldier, for example, is a networked computer disguised as a helmet. Last week, at the Congress on the Future of Engineering Software 2011 (COFES), Joseph Juhnke, president and CEO of Tanagram Partners, shared his firm’s works for the Defense Advanced Research Project Agency (DARPA).
Augmented Reality for Combat
The headgear, part of Tanagram’s iARM (Intelligent Augmented Reality Model) solution for DARPA, “encompasses an open source operating system supporting geolocation and triangulation, together with data services that integrate voice, video, and image for facial/object recognition and pattern analysis. It is supported by a hardware platform integrating a computer processor, encrypted wireless, camera/video and visual display,” explained Tanagram.
Juhnke is now working on developing the same type of equipment to firefighters. In cases where users must navigate through smoke-filled room with little or no visibility, point-cloud or mesh data of the building may become the primary path-finding option. Tanagram uses Bloom Server, a geo-social asset management platform, as the engine behind its augmented reality platform. In addition to hosting and delivering data sets, Bloom Server may also be used to aggregate and turn 2D photos into point cloud data in 3D. (The point cloud making up a building’s facade, for example, may be extracted out of 30-40 photos of the same facade, taken from varying angles.)
“As our effort continues we will be entering the second phase of our program that will include the development of the user interface for the iARM platform. That user interface will be a multichannel input / output leveraging gesture (hands/hand symbols), speech, and context,” Juhnke wrote in the company’s blog.

Bacteria for Data Storage
Can you imagine ordering a CAD software package and receiving a swab of E. Coli? You might, if 11 students at the Chinese University of Hong Kong make swift progress in their research. Alan Yu, one of the Ph. D. students who have been exploring the idea of “biostorage,” flew to Phoenix, Arizona, last week to give a presentation at COFES 2011.
Yu and his colleagues have figured out a way to deposit encrypted data into bacteria as DNA. If you’re not satisfied with current USB drives’ storage capacity, you’d be glad to know that, according to the press release from the university, “With this technology, it is estimated that one gram of bacteria can store data of up to 900,000 GB (gigabytes), which is equivalent to 450 hard drives, each with 2 TB (terabytes) of storage capacity.”
“Bacteria can’t be hacked,” Yu pointed out. “All kinds of computers are vulnerable to electrical failures or data theft. But bacteria are immune from cyber attacks. You can safeguard the information.”
But don’t expect petri dishes to begin appearing in HP and Dell workstations. By the students’ own admission, this method still presents quite a bit of challenge, especially in data extraction. Currently, it’s a process that needs to be completed in a lab with expert help.
COFES is an annual event hosted by Cyon Research, a think-tank that focuses on engineering and analysis software. The event is by invitation only, primarily targeting decision-makers in the manufacturing, architectural, and plant design markets.
Subscribe to our FREE magazine, FREE email newsletters or both!
Latest News
About the Author
Kenneth Wong is Digital Engineering’s resident blogger and senior editor. Email him at [email protected] or share your thoughts on this article at digitaleng.news/facebook.
Follow DE