
Top Story
How to Optimize Manufacturing Capacity
April 6, 2023
Use of virtual manufacturing networks has potential to lead to greater agility and resilience in the long run.
AI, Cybersecurity Skills Offer Opportunity for Small Biz, Survey Says
February 13, 2024
Dassault Systèmes survey of 1,000 employees in the technology sector in the U.S. and Europe reveals trends in artificial intelligence, skills gaps and digital transformation.
Authentise Gets Funding for Cybersecurity in Additive Initiative
February 6, 2024
The R&D funding was given with intent to enhance cybersecurity in the U.S. manufacturing sector.

How to Optimize Manufacturing Capacity
April 6, 2023
Use of virtual manufacturing networks has potential to lead to greater agility and resilience in the long run.
Karamba Security Joins Siemens Digital Industries Software Solution Partner Program
December 8, 2022
Under the automotive cybersecurity regulation (UN R155) and standards (ISO/SAE 21434), automotive manufacturers can accelerate the introduction of cybersecurity into connected vehicles.

Connected Medical Devices Come into Their Own
August 4, 2022
The internet-enabled healthcare ecosystem encompasses sensors, devices and other systems able to acquire, process and transmit health data.
MxD Names Berardino Baratta as New CEO
July 1, 2022
Current VP of Projects and Engineering transitions into leadership role.
Atos and Dassault Systèmes Join Forces to Deliver Sovereign Cloud Platform Experience
December 14, 2021
Clients can benefit from the combination of Dassault Systèmes’ 3DEXPERIENCE platform on the cloud and Atos’ OneCloud Sovereign Shield, according to the companies.

Additive Manufacturing 2.0: Building a Resilient, Diverse, Secure Supply Chain
May 17, 2021
A new executive order and cybersecurity concerns shine light on the state of 3D printing.

Safeguarding Engineering in the Work-from-home Era
April 1, 2021
Securing design data requires a holistic approach that includes both technology and good policies.

UT San Antonio Launches Cybersecurity Manufacturing Innovation Institute
December 7, 2020
ORNL to apply communications security, digital manufacturing expertise to new DOE Cybersecurity Manufacturing Innovation Institute.
MxD releases the Hiring Guide: Cybersecurity in Manufacturing
August 28, 2020
A free webinar on the guide will be held Sept. 3 at 10 a.m. CT.
Security in the Era of Cloud
March 1, 2020
Stolen credentials are a greater threat than stolen laptops.
Industrial Internet Consortium Publishes the Data Protection Best Practices White Paper
July 22, 2019
Guidance designed to help ensure data security, privacy and trustworthiness.
Encrypted Sensors Has Programmed Encryption onto FPGA Hardware Chip
May 7, 2019
The company says it has applied to trademark it as an actual private network.
Manufacturing Industry Vulnerable to Cyberattack
December 1, 2018
The industry is becoming increasingly susceptible to such attacks as additive manufacturing (AM) gains wider acceptance, bringing with it a more decentralized approach that allows for companies to manufacture when and where needed.
Latest News
AMGTA Shares Findings on Sustainability of Powder and Wire Additive Feedstock
Research indicates, for one, that from an energy perspective, helium is the most sustainable method of gas atomization for metallic...
MATLABS Features Modelithics EXEMPLAR Library
Library for MATLAB includes almost 50 Microwave Global Models representing nearly 3,500 components for many component suppliers, company says.
Fictiv Demonstrates New AI Capabilities
Tool enables an upgrade of material selection for production parts.
ADDMAN Earns Qualification Project for U.S. Navy
This project focuses on the additive manufacturing (AM) of copper-nickel (CuNi) components in submarine fittings.
FREE WEBINAR May 7: Addressing the Skilled Worker Shortage with Customized eLearning
In this webinar, you can find out how eLearning and learning management software can help companies fill the skilled trades...
America Makes’ Spring 2024 TRX Explores AM Advancements
The event was a knowledge hub for industry leaders to network and share innovative approaches across design, material, process and...
All posts
New & Noteworthy

New & Noteworthy: Safe, Cost-Effective Metal 3D Printing - Anywhere
Desktop Metal’s Studio System offers turnkey metal printing for prototypes and...
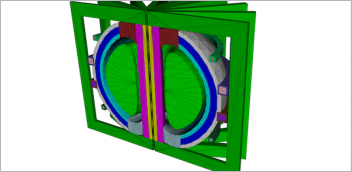
New & Noteworthy: Direct Neutronics Analysis on CAD
Coreform Cubit 2023.11 workflows enable neutronics directly on CAD for next-generation nuclear energy...
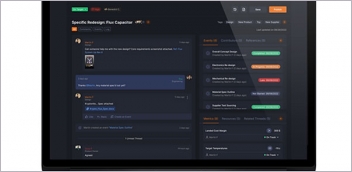
New & Noteworthy: Agile Engineering Collaboration
Authentise Threads is a new software tool for distributed communications and project...

New & Noteworthy Product Introduction: Enterprise VR Headset
Lenovo ThinkReality VRX has an immersive display works with virtual, augmented and...
